foundation
PURPOSE
Welcome on the CYBNITY technical documentation. The implementation documentation includes many types of support deliverables produced during the software development life cycle. You can find documentations relative to software maintenance like:
- Design diagram regarding software source codes;
- User interfaces prototypes;
- Support to software build process and packaging;
- Systems configuration and deployment procedure.
These technical documentations are supporting the functional, architectural and/or organizational documentations available on CYBNITY Universe public web site about concept, requirements, business/technology/systems architectures…
DEVELOPMENT DOCUMENTATIONS
COMPONENTS & SYSTEMS BUILD
Software Design
- Architecture Models presenting the systems and general description about components.
- UML documentation presenting the domain analysis, and the software specifications over several views according to an Unified Process (UP) approach (e.g Use case view, Design view, Deployment view, Implementation view and Process view).
Build Standards
Supported by industrialization platform including several factory tools, several CYBNITY standards and guidelines are applied as Continuous Integration (CI) protocol via pipeline models:
- Commit Stage Pipeline Model
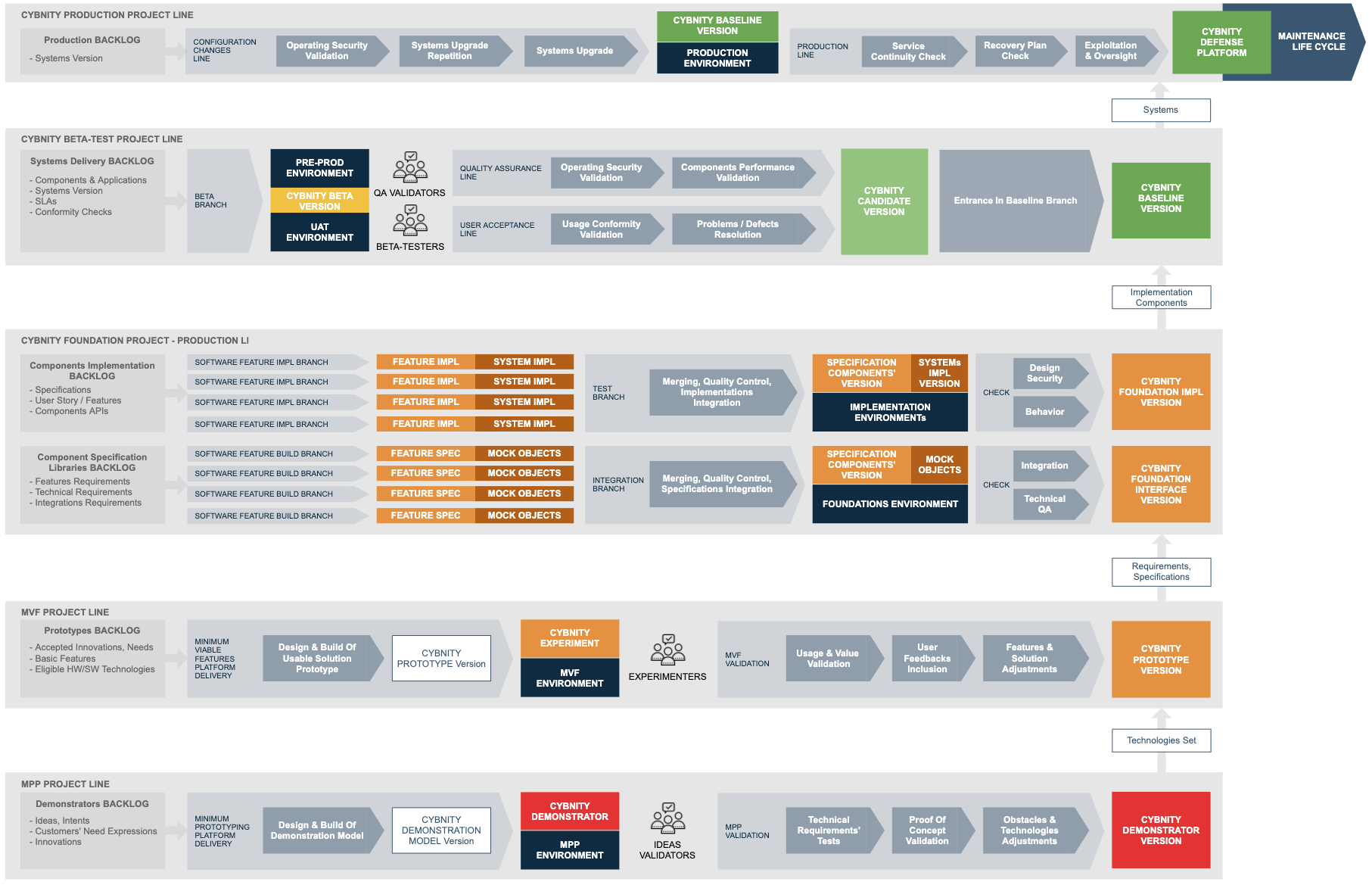
Components, Systems & Solutions Delivered
The build and delivery of the CYBNITY systems’ features is performed through several sub-projects dedicated to specific activities and/or outputs:
- CYBNITY Demonstrator versions via MPP Project Line
- CYBNITY Prototype versions via MVF Project Line
- CYBNITY Implementation Components versions via Foundation Project Production Line
- CYBNITY validated Systems versions via Beta-Test Project Line
- CYBNITY Defense Platform versions via Production Project Line
DELIVERY DOCUMENTATIONS
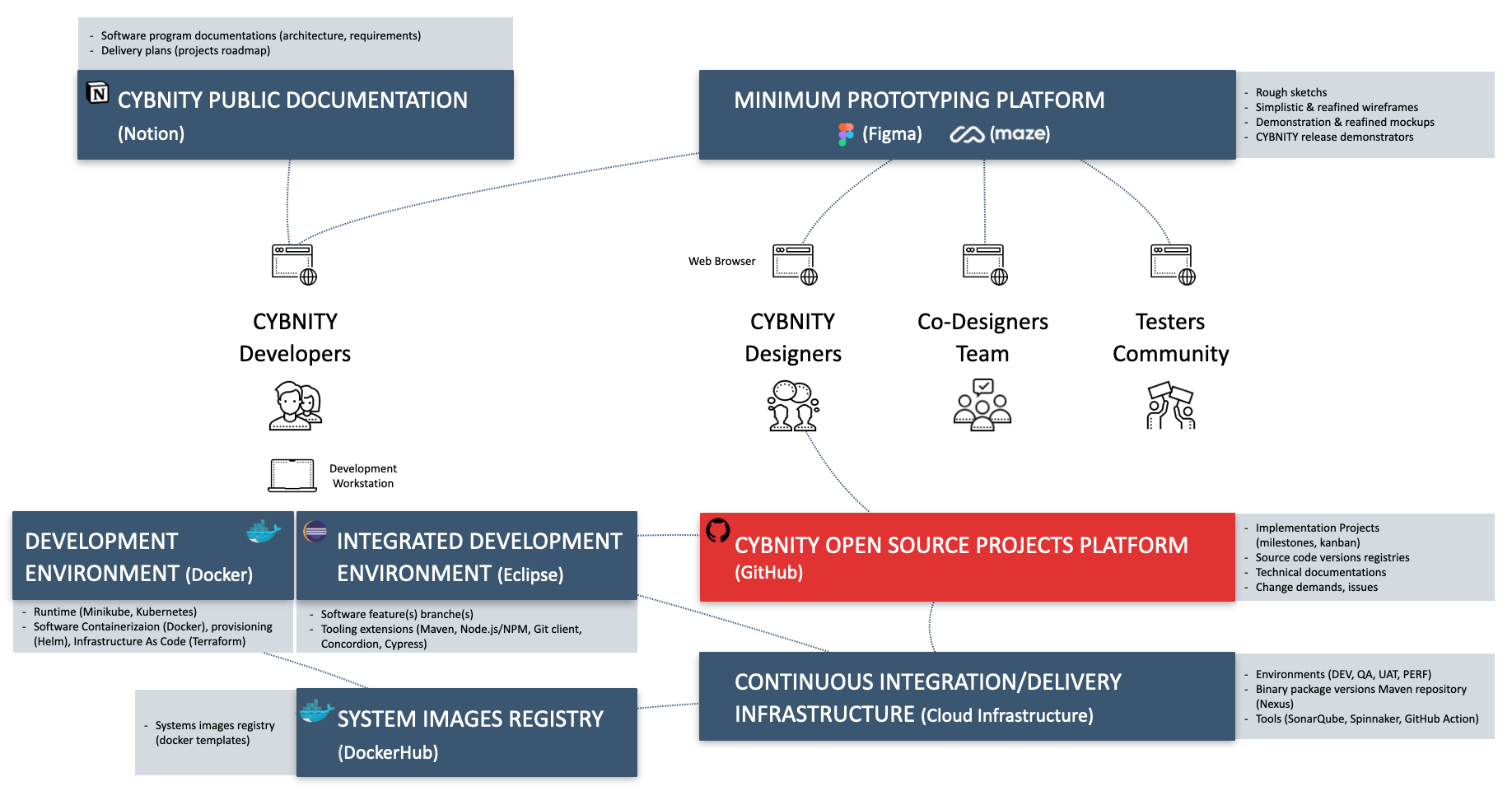
COLLABORATIVE WORKSPACES
SOFTWARE ARTIFACTS FACTORY
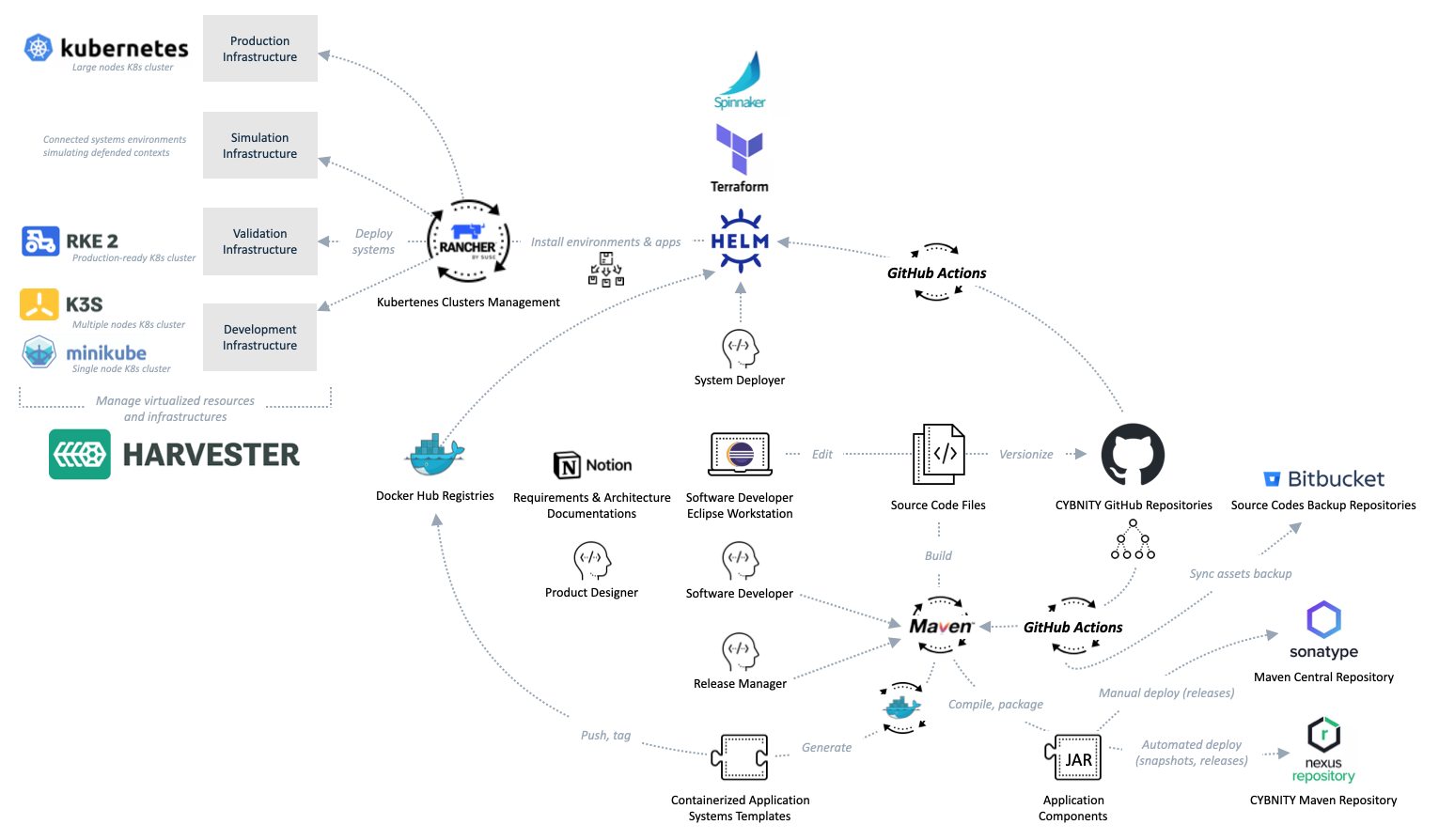
Resources Infrastructure
CYBNITY project is managing a resources infrastructure of servers dedicated to open source project development, which can serve as example for other companies in terms of hardware and/or virtualized resources supporting the deployment of CYBNITY environment modules:
Support and How-To
- Developers How-To: guides about tools, tasks organization and other assistance documentations helping a developper to contribute.
SYSTEMS & ENVIRONMENTS DELIVERY
Systems Deployment Standards
Supported by industrialization platform including several factory tools, several CYBNITY standards and guidelines are applied as Continuous Delivery (CD) protocol via pipeline models:
- Releasing Pipeline Model
- Deployment Pipeline Model
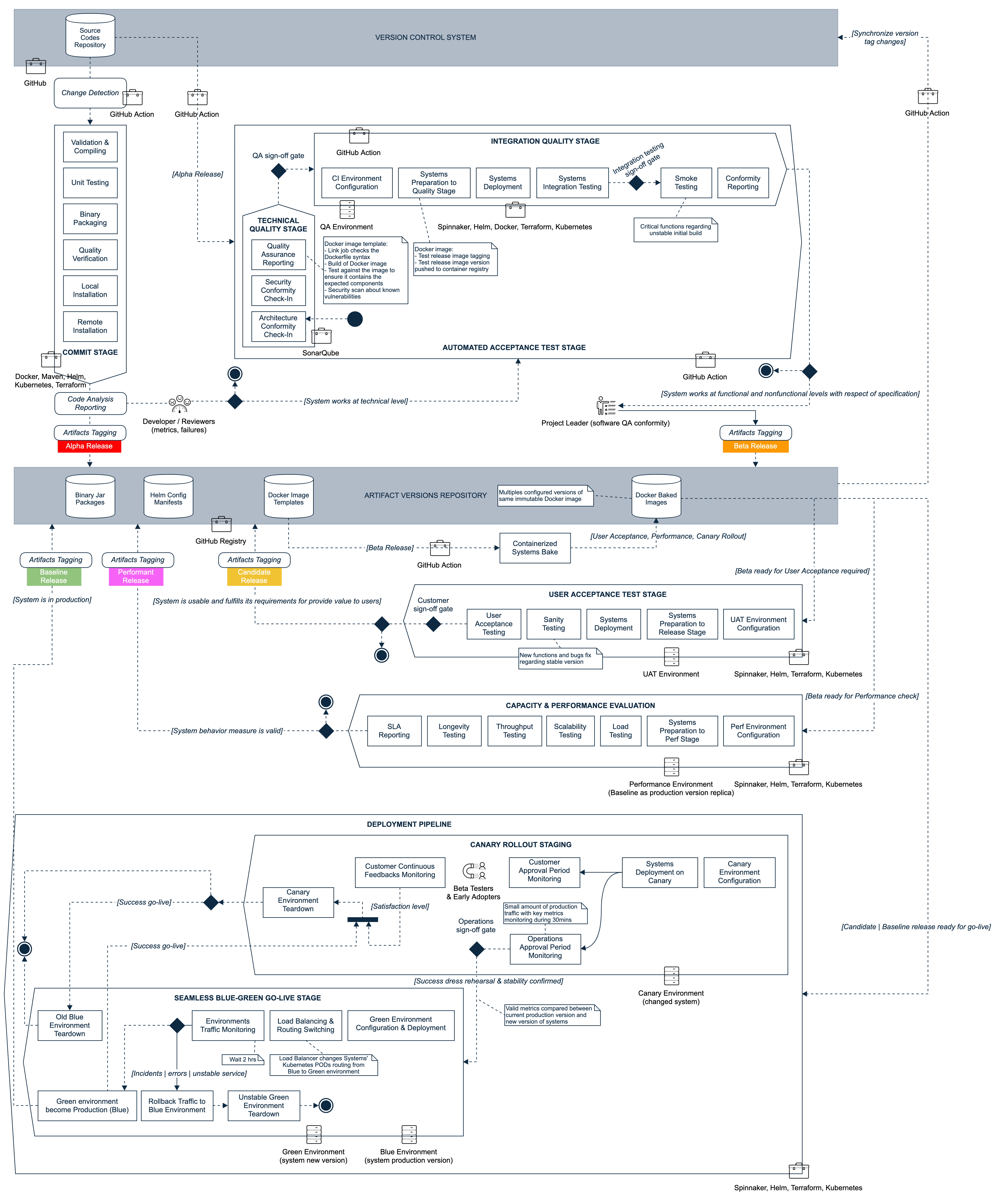
Systems Configuration
The branching strategy including the practices and usage rules that should be followed by the developers are presented in detail on CYBNITY software configuration and integration management model
Continuous Integration Chain
Applications Operating
QUALITY CONTROL
Several quality scopes are considered during the development and operating of delivered systems. They are formalized via requirements defined and controlled by project team with validation protocols and quality measures.
| REQUIREMENTS TYPE | SCOPE & DESCRIPTION | QUALITY VALIDATION | QUALITY SCORING |
|---|---|---|---|
| Functional | Application features behavior. See Information systems requirements | Integration tests, non-regression tests, usage acceptance tests (UAT) | Anomalies (deviation from a rule) and defects (fault/malfunction) count/trend |
| Security | Software and system security concepts and control measures implemented by the asset. See Software development requirements based on NIST SP800-218 Secure Software Development Framework (SSDF) | Technical & non technical measures tests, third-party audit (e.g regulation), NIST certification | NIST Cybersecurity Framework (CSF) maturity level state, anomalies count/trend, security incidents (e.g Confidential, Integrity, Availability violations) and defects (e.g malfunction of security measure) count/trend |
| Maintainability | Software source codes readability and complexity level, design and implementation architecture, language patterns, documentation level of functional/technical implementation. See Architecture requirements based on NIST SP800-27 Engineering principles | Unit tests, code quality check (e.g automated and/or manual reviews) | Anomalies and defects count/trend |
| Operating | Deployment documentation and procedures, tools compatibility, applications configuration, administration capabilities and support elements | Technical review, repetition tests | Problems and incidents count/trend |
| Observability | Monitoring capabilities, supervision features (e.g robustness capacity level, resources allocation trend), metrics (e.g application usages, performance level) | Monitoring tests | Anomalies and defects count/trend |